The access to Collage Web data is authorized based on the Magnet Enterprise user accounts and the active organization. New user accounts and organizations are managed in the Topcon Enterprise and Magnet Enterprise sites. For details, please refer to each site's accompanying documentation.
Users in an administrative role must assign the right permissions to all other users that belong to their organization.
In addition, regular users control access to the objects (layers and projects) they create.
Authorization can be managed for both groups and individual users. Please note that groups defined in Collage Web are not related to Magnet Enterprise teams.
In addition, it is important to distinguish two levels of authorization management:
All users in the organization are added to a default Demo group when they enter Collage Web for the first time. In this way, they can see the demonstration project and layers. It is recommended to keep this group. Do not manually change its members or modify the group permissions.
To manage authorization for non-administration users, it is recommended to create other groups with different purposes (e.g. data uploaders, editors, etc.) and set permissions for each group. A user can belong to multiple groups and inherit all their permissions.
If necessary, exceptions can be added to allow or deny specific permissions to individual users.
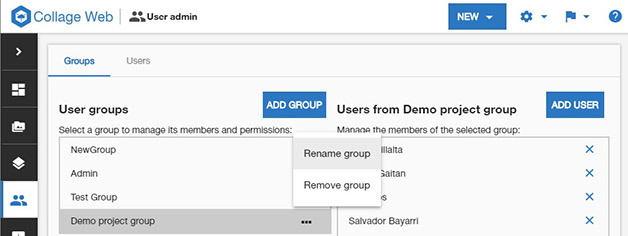
The Authorization Management page can be accessed from the "User admin" icon in the application menu. If a user does not see this menu, it means he/she does not have enough permissions to see and manage groups, users and authorization information in the active organization.

In this tab (see image above), users can manage groups and assign generic permissions to them.
It is recommended that administrative users create groups to manage authorizations in the organization, instead of setting permissions for each individual user. One user can belong to multiple groups.
Usually, a Demo group will be created by default, to allow all organization users to view Collage Web demo data.
The page includes buttons to create new groups and add users to them. A context menu can be used to rename and delete the selected group.
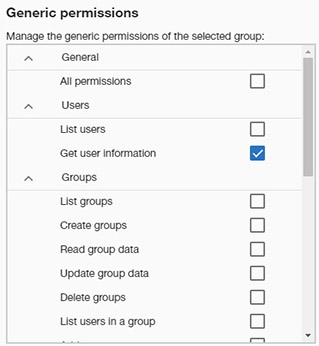
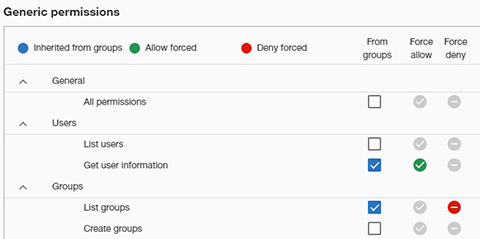
This panel helps user to assign generic permissions related to different application and management operations. Permissions are granted to the selected group by switching on the corresponding checkbox.
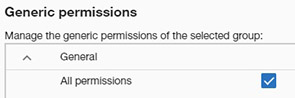
If the user want to grant all permissions to the group, he/she can do so by checking the "All permissions" item. In this case, the rest of items are hidden.
This is the list of generic permissions and their meaning:
| Permission | Meaning |
|---|---|
| Users: List users. | Permission to get the list of all users in the organization. This permission will allow the selected group or user to see this list in the "User admin" page. |
| Users: Get user information. | This permission is needed to perform user management tasks. |
| Groups: List groups. | Permission to get the list of all groups defined in the organization. This permission will allow the selected group or user to see this list in the "User admin" page. |
| Groups: Create groups. | Permission to create new groups. |
| Groups: Read group data. | Permission to read individual group data, needed for group management. |
| Groups: Update group data. | Permission to change internal group data, needed for group management. |
| Groups: Delete groups. | Permission to remove existing organization groups. |
| Groups: List users in a group. | Permission to see a list of all users in a group. Needed for managing the users who belong to each group. |
| Groups: Add users to a group. | Permission to add a new user to a group. |
| Groups: Remove users from a group. | Permission to remove a user from the list of users of a group. |
| Permission management: List generic permissions of users. | Permission to see which generic permission a user has. |
| Permission management: Add generic permissions to users. | Permission to grant a generic permission to a user. |
| Permission management: Remove generic permissions from users. | Permission to deny a generic permission to a user. |
| Permission management: List generic permissions of a group. | Permission to see which generic permission a group has. |
| Permission management: Add generic permissions to a group. | Permission to grant a generic permission to a group. |
| Permission management: Remove generic permissions from a group. | Permission to deny a generic permission to a group. |
| Object access: Add object access permissions to users. | Permission to authorize users to access individual objects like projects, layers and categories. |
| Object access: Remove object access permissions from users. | Permission to deny users access to individual objects like projects, layers and categories. |
| Object access: Add object access permissions to groups. | Permission to authorize groups to access individual objects like projects, layers and categories. |
| Object access: Remove object access permissions from groups. | Permission to deny groups access to individual objects like projects, layers and categories. |
| Notification: List event log. | Used only for testing purposes. Not needed by regular users. |
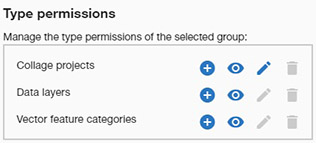
This panel controls the generic access to objects (projects, layers and categories) for the selected group. From left to right, the icons specify the Create, View, Edit/Update and Delete permissions for each object type.
Users inherit their permissions from the groups they belong to. For instance, if a user belongs to group A and group B, he/she will get all permissions from group A plus all permissions from group B.
However, in the Users tab, exceptions can be created for individual users to override the permissions inherited from the groups, by adding more permissions or denying them.
First, the user must be selected. The panel will show which groups he/she belongs to.
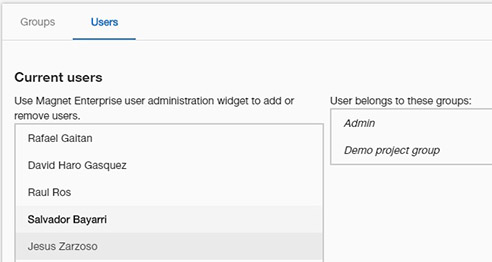
In this panel, we can see (in blue) the permissions the selected user inherits from the groups. We can add an exception (in red) to deny these permissions. In a similar way, we can grant an additional permission (in green) to the user, even if it's not inherited from the groups.
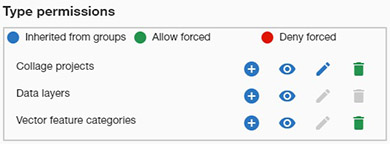
Similarly, exceptions can be added to the Type permissions. The panel shows (in blue) those permissions granted by the groups the user belongs to, but we can add other permissions (in green), or deny the inherited ones (in red).
Objects (projects, layers and categories) which are created in one organization are never visible to other organizations. In order to share information with users from another company, they must be invited into our organization. In addition, they must select our organization as the active one before logging in Magnet Enterprise, and these users must have a license of Collage Web assigned to them.
Within the organization, generic Type permissions (see above) control the overall access of groups and specific users to the different object types. However, these general authorization can be adjusted for each data object.
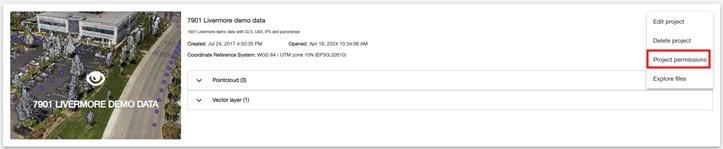
For Projects, the user can edit access permissions from a project's menu in the Projects page and from the Preferences panel in the Project Viewer.
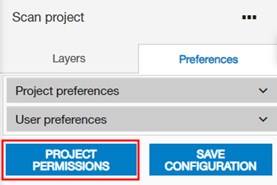
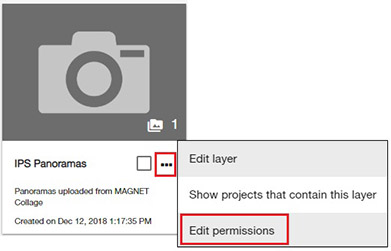
For Layers, the user can edit access permissions from each layer's context menu in the Layers page and from the layer's menu in the Layers tab of the Project Viewer.
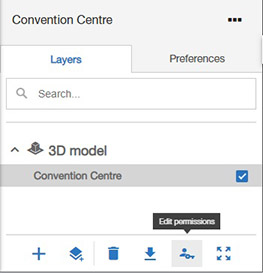
For Categories, the user can edit their access permissions in the Category Manager, which opens from the Layers tab in the Project Viewer.
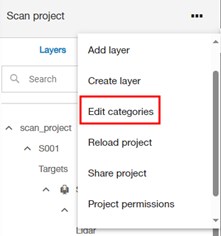
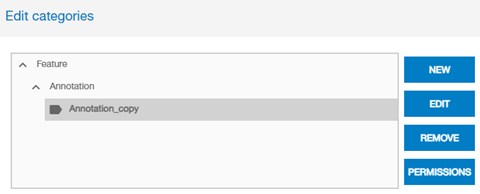
After selecting the corresponding object Permissions menu or button command, the Permission Editor dialog will open. In this dialog, the user can assign group access to the object, and specific exception to user access can be set to override the group access permissions.
Three levels of access are possible:
For instance, in the sample image below, the Editor group has Update level access, but a special restriction has been added to one user to prevent him/her from editing the object. He/she will only be able to view it.
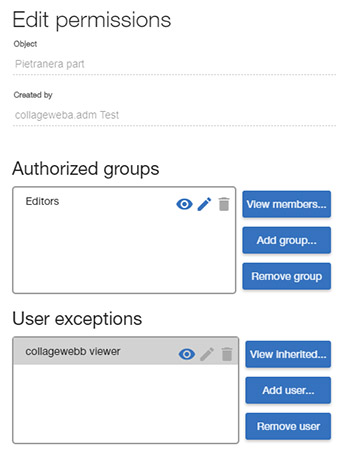
Note that: